Protecting Your Business from Cyber Breaches: Lessons from M&S, Co-op and Harrods
The recent cyber-attacks targeting major UK retailers serve as a stark reminder that no business is immune to digital threats. Strengthening your
IT Security is essential, here’s how your organisation can avoid becoming the next headline.
The Wake-Up Call: UK Retail Sector Under Attack – An IT Security Crisis
The cyber breaches at Marks & Spencer, Co-op, and Harrods sent shockwaves through the UK business community. These attacks weren't just isolated incidents but rather a clear signal that cybercriminals are actively targeting retailers with increasingly sophisticated methods. What's particularly concerning is that these weren't small businesses with limited resources—these were established giants with substantial security budgets.
So, what went wrong? And more importantly, how can your business avoid the same fate?
Four Urgent Actions to Protect Your Business
1. Prioritise Security Risk
The UK retail breaches exploited weaknesses that could have been identified through comprehensive risk assessment. Focus on your most valuable data assets and critical systems first.
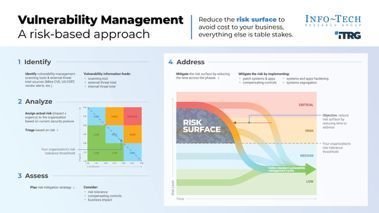
A systematic approach to identifying vulnerabilities before cybercriminals do is no longer optional—it's essential for business survival.
Vulnerability management does not always equal patch management. There is more than one way to tackle the problem, particularly if a system cannot be easily patched or replaced. If a vulnerability cannot be completely remediated, steps to reduce the risk to a tolerable level must be taken.
What you should do:
- Review your vulnerability management procedures and implement risk-based vulnerability management that prioritises remediation based on genuine threat levels
- Build and present a risk-based security budget that aligns with actual threats Communicate security needs effectively to executive stakeholders to secure proper funding
2. Improve Identity and Access Management
Multi-factor authentication is one security control could prevent approximately 80% of common breach scenarios. The recent retail breaches demonstrated how outdated systems and poor access controls can be devastating entry points. These breaches may also have exploited MFA vulnerabilities to gain access
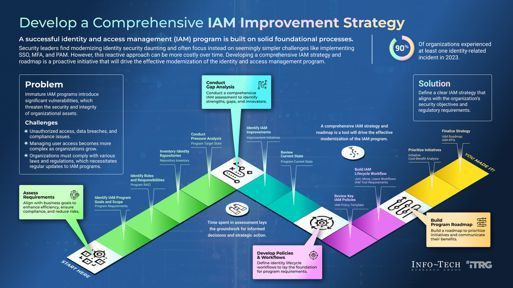
What you should do:
- Review your authentication schemes to eliminate SMS token delivery, use a secure app or token device instead.
- Enforce MFA across all systems, especially for remote access and privileged accounts
- Develop a comprehensive Identity and Access Management (IAM) strategy built on solid foundations
- Regularly audit who has access to what and whether that access is still necessary
Remember: The strongest lock is useless if you're handing out keys to everyone.
3. Develop and Test Your Incident Response Plan
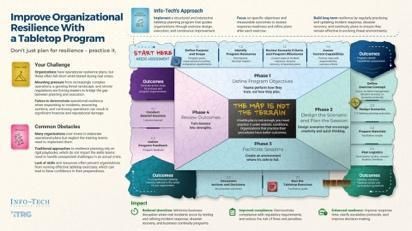
Recent retail breaches have shown that detection time and response quality directly impact financial damage. When (not if) a breach occurs, your ability to respond quickly and effectively will determine the outcome.
What you should do:
- Improve organisational resilience with regular tabletop exercises
- Practice your procedures under realistic conditions—organisations that rehearse have demonstrably better outcomes
- Create a scalable incident response program that doesn't break the bank
An untested incident response plan is merely wishful thinking. Your team needs to build muscle memory for crisis situations.
4. Train Your Staff Continuously
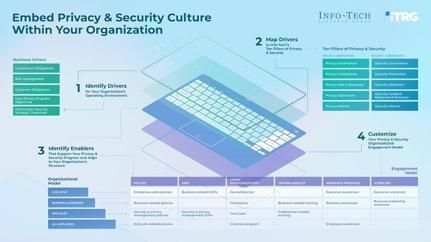
Human error remains a primary entry point for attackers targeting UK retailers. Your cybersecurity is only as strong as your least security-conscious employee.
What you should do:
- Build a plan to close cybersecurity competency gaps across your organisation
- Develop business-aligned security competencies for your IT team
- Upskill your team beyond mere certifications—focus on practical competence
- Run regular, engaging security awareness training that reflects current threats
Beyond Protection: Know Where You Stand
Thinking your organisation is sufficiently protected against security threats isn't good enough. You need to know.
This is where KH Infosec's IT Security Diagnostic Program provides invaluable insight. Our low-effort, high-impact program helps security leaders assess and improve their security practices through three critical steps:
1. Assess Current Operations Based on Best Practices with our Governance & Management Scorecard
2. Measure Business Satisfaction and Identify Security Needs with our IT Security Business Satisfaction & Alignment tool
3. Improve Targeted Information Security Areas with our Security Process & Technology Effectiveness assessment
The diagnostic programme powered by InfoTech Research Group covers everything from governance and management to specific security domains including server security, end-user device security, network security, and data protection.
Our data-driven programs ask business and IT stakeholders the right questions to ensure you have the inputs necessary to build an effective IT strategy.
See how you stack-up against your peers or against the InfoTech Research Group database of over 60,000 respondents from over 2,000+ organizations worldwide.
The cyber breaches at M&S, Co-op, and Harrods weren't inevitable—they were the result of security gaps that could have been addressed proactively.
Is your business next? Or will you take the necessary steps to protect your organisation before a breach occurs?
Book a free half hour consultation to schedule your IT Security Diagnostic and discover how KH InfoSec in partnership with Info~Tech Research Group can help you develop the critical cyber resilience strategy and insights that breached companies consistently report they wished they had before incidents occurred.
Click here Find out more about KH Infosec partnership with Info-Tech Research Group
Download sample Diagnostic Programme Reports Below:
Download Security Effectiveness - Sample Report
Download Security Business
Satisfaction and Alignment Sample
Don't Wait for Your Wake-Up Call
Remember: In cybersecurity, resilience is not just better than cure—it's the difference between business continuity and potentially devastating consequences.

#SecurityDiagnostic #CyberThreat2025 #RetailBreaches #RetailCyberAttack #RetailSecurity #CyberSecurity #CyberResilience








